Figure:
The activity diagram of STILL system
|
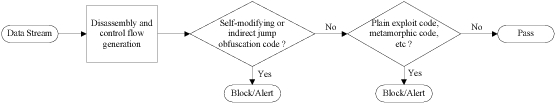
Figure ![[*]](/usr/share/latex2html/icons/crossref.png) depicts how STILL works.
We next briefly describe its working flow. It works as a
proxy-based blocker in the application layer. When it captures a
data stream, it disassembles the data stream and generates a
control flow graph. It analyzes the disassembled result in two
stages. First, STILL detects self-modifying and indirect jump
obfuscation code. Although the real exploit code may be hidden by
self-modifying and indirect jump, the obfuscation code itself
provides some strong evidences of self-modifying and/or indirect
jump behaviors. STILL detects these behaviors by static taint
analysis and initialization analysis. Since polymorphism is a kind
of self-modifying, STILL can also detect polymorphic code in this
stage. However, attackers may use neither self-modifying nor
indirect jump obfuscation. In the second stage, STILL detects the
plain exploit code based on system calls and/or function calls
that could even have been obfuscated by metamorphism. STILL also
exploits static analysis and initialization analysis in this stage
to combat other obfuscation techniques. Below we will describe the
mechanisms in greater details.
depicts how STILL works.
We next briefly describe its working flow. It works as a
proxy-based blocker in the application layer. When it captures a
data stream, it disassembles the data stream and generates a
control flow graph. It analyzes the disassembled result in two
stages. First, STILL detects self-modifying and indirect jump
obfuscation code. Although the real exploit code may be hidden by
self-modifying and indirect jump, the obfuscation code itself
provides some strong evidences of self-modifying and/or indirect
jump behaviors. STILL detects these behaviors by static taint
analysis and initialization analysis. Since polymorphism is a kind
of self-modifying, STILL can also detect polymorphic code in this
stage. However, attackers may use neither self-modifying nor
indirect jump obfuscation. In the second stage, STILL detects the
plain exploit code based on system calls and/or function calls
that could even have been obfuscated by metamorphism. STILL also
exploits static analysis and initialization analysis in this stage
to combat other obfuscation techniques. Below we will describe the
mechanisms in greater details.
Subsections
xinran wang
2008-02-28